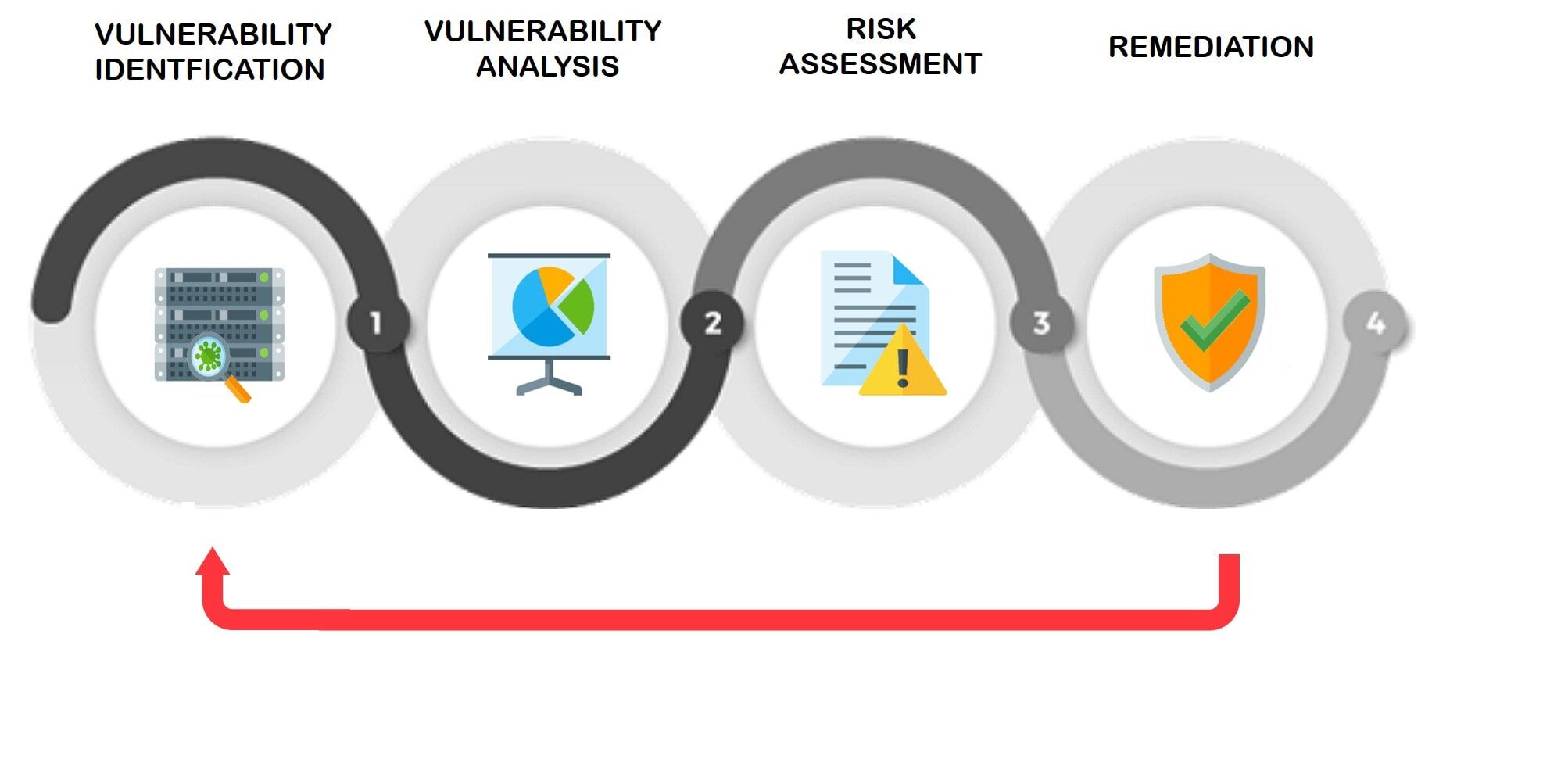
A security vulnerability is a weakness or flaw in a system that can be exploited to gain unauthorized access or cause damage. Vulnerabilities exist in software, hardware, networks, and human processes. Some common types of security vulnerability tools include:
- SQL injection – Allows malicious SQL statements to be inserted into an entry field that can read/modify data or execute commands.
- Cross-site scripting (XSS) – Enables attackers to inject client-side scripts into web pages viewed by other users. Can be used to bypass access controls or conduct phishing attacks.
- Buffer overflow – Occurs when a program tries to store more data in a buffer (temporary data storage) than it was intended to hold. This can cause crashes and allow arbitrary code execution.
- Privilege escalation – Exploits bugs or design flaws to gain elevated access to resources that are normally protected.
- Default/weak passwords – Using easily guessed login credentials or keeping default passwords set by vendors. Allows unauthorized access.
Some infamous examples of major vulnerabilities include:
- Heartbleed – A bug in OpenSSL cryptography library that allowed theft of encrypted data from services using OpenSSL.
- Shellshock – A Bash shell vulnerability that enabled arbitrary code execution via environment variables.
- Meltdown/Spectre – Design flaws in CPUs that allowed bypassing memory isolation mechanisms.
Vulnerabilities are continuously being discovered and disclosed. Keeping systems patched and updated is crucial for security. Vulnerability scanning tools are important for proactively finding and fixing flaws before they can be exploited.
Table of Contents
Why You Need a Security Vulnerability Tools Scanner
Vulnerability scanning is a critical part of any organization’s security strategy. Here are some of the key reasons why you need a security vulnerability tools:
- Identify vulnerabilities and risks in applications/networks – Scanners can crawl your entire network infrastructure and applications to discover vulnerabilities that could be exploited by attackers. This allows you to proactively find and fix security holes before they are taken advantage of.
- Prioritize which vulnerabilities to fix first – Scanners provide risk scores for vulnerabilities so you can focus on fixing the most critical ones first. This helps you get the biggest security bang for your buck.
- Continuous monitoring and alerts – The most advanced scanners continuously monitor for new vulnerabilities and send alerts when any are found. This ensures you are always aware of the latest threats.
- Meet compliance requirements – Many industry regulations and standards like PCI DSS require regular vulnerability scanning. Using a scanner provides audit reports to prove compliance.
Vulnerability management is vital for reducing your organization’s attack surface. A robust security vulnerability tool arms you with the knowledge you need to harden your security posture and stop threats in their tracks. Prioritizing this area will pay dividends in keeping your data, systems and customers safe.
Types of Security Vulnerability Tools Scanners
There are several ways to categorize vulnerability scanners:
Network Based vs Host Based
- Network based scanners assess vulnerabilities from outside the network by scanning IPs and ports. They don’t require installation on each host.
- Host based scanners run locally on each host, scanning from the inside. They provide visibility into the OS and apps.
Commercial vs Open Source
- Commercial scanners like Tenable, Qualys, and Rapid7 offer robust features but require purchasing a license.
- Open source scanners like OpenVAS and Nessus Home are free but have limited functionality.
Active vs Passive
- Active scanners probe systems and analyze responses to find weaknesses. This can impact performance.
- Passive scanners silently monitor traffic flow without sending probes. Less intrusive but less comprehensive.
Credentialed vs Non-Credentialed
- Credentialed scanners authenticate using admin credentials to access non-public info. More thorough but higher risk.
- Non-credentialed scanners don’t use credentials. Limited visibility but lower impact on systems.
Key Features of Vulnerability Scanners
Vulnerability scanners have several key features that make them valuable security tools:
Vulnerability Detection and Reporting
The primary function of a security vulnerability tools is to identify security flaws in networks, systems, and applications. It does this by scanning assets and comparing configurations against a database of known vulnerabilities. The scanner generates detailed reports highlighting vulnerabilities found, along with severity ratings and remediation advice. This helps security teams understand their organization’s risk exposure and prioritize patching.
Risk Scoring and Prioritization
Advanced scanners can assign risk scores to vulnerabilities based on the likelihood of exploitation and potential business impact. This allows IT security staff to focus on fixing the most critical flaws first. Risk scoring uses factors like vulnerability type, asset value, and exploit availability.
Configuration Auditing
Scanners also audit system configurations by checking them against best practice benchmarks. This reveals configuration issues that could introduce risk even if there is no known exploit. It helps enforce organizational security policies and compliance mandates.
Integration with Bug Trackers/SIEMs
Quality scanners integrate with bug tracking/ticketing systems like Jira and SIEM platforms like Splunk. This allows seamless tracking of identified weaknesses through remediation. Alerts can also be sent to SIEMs when critical vulnerabilities are discovered.
Scheduling and Automation
Scans can be scheduled to run on a regular basis to identify new vulnerabilities that arise over time. Scheduling and automation features make testing more consistent and efficient. Scans can also be triggered by certain events or integrated into the SDLC.
Selecting the Right Vulnerability Scanner
Choosing the right security vulnerability tools for your needs requires careful evaluation of several factors:
- Scan Speed and Accuracy – Look for scanners that perform checks rapidly without sacrificing detection rates. Speed is important for regular scans, while accuracy ensures you capture the most vulnerabilities. Prioritize scanners with high speed and accuracy.
- Breadth of Checks – The best scanners check for vulnerabilities across web apps, networks, databases, configuration issues and more. Evaluate the breadth and depth of checks to ensure the scanner fits your environment.
- Ease of Use – Consider how easy the scanner is to deploy, run scans and generate reports. Look for intuitive interfaces, pre-configured scanning templates and clear reports. Tools that are simple to operate will encourage consistent use.
- Regulatory Compliance – If your organization needs to comply with standards like PCI DSS, HIPAA or NIST, ensure your scanner includes the necessary built-in compliance checks to meet requirements.
- Integrations – Determine if the scanner integrates with other security tools you use like SIEM, firewalls, bug trackers and ticketing systems. Integrations allow seamless workflows.
Carefully weighing these key factors will help you select an advanced vulnerability scanning solution tailored to your unique security needs and environment. The right scanner provides maximum coverage, accuracy and usability for hardening your attack surface.
Popular Security Vulnerability Tools
Security vulnerability tools have become an essential tool for identifying security flaws and misconfigurations. There are many options on the market, but some of the most popular and widely used security vulnerability tools include:
Nessus
Nessus is a security vulnerability tools which is one of the most well-known and widely used vulnerability scanners. Originally developed by Tenable Network Security, it was recently acquired by Peraton. Nessus scans networks for vulnerabilities, misconfigurations, and exposures. It has a user-friendly interface and provides detailed reports on discovered issues. Nessus is highly customizable and scalable.
OpenVAS
OpenVAS (Open Vulnerability Assessment System) is a security vulnerability tools which is free and open source vulnerability scanner managed by Greenbone Networks. It scans for thousands of vulnerabilities and is frequently updated. OpenVAS provides scheduled and distributed scanning options. It generates detailed reports with severity ratings and remediation advice.
Qualys
Qualys is a security vulnerability tools which offers an all-in-one cloud-based IT, security and compliance solutions. Their vulnerability management scanner allows organizations to continuously monitor their IT assets for vulnerabilities. Qualys provides pre-defined assessments as well as custom scans. It has robust reporting and integration capabilities.
Tenable.io
Tenable.io, is a security vulnerability tools which is formerly known as Nessus Cloud, is a vulnerability management platform offered as software as a service. It provides agent-based and agentless vulnerability scanning of assets including networks, containers, web applications and cloud environments. Tenable.io offers predictive analytics to help prioritize vulnerabilities.
Rapid7 InsightVM
Rapid7 InsightVM (formerly Nexpose) is a security vulnerability tools which provides vulnerability assessment and management solution that scans networks, endpoints, cloud, containers and web applications. It provides actionable reports, risk-based vulnerability management, and integrates with other Rapid7 solutions. InsightVM enables organizations to identify and prioritize vulnerabilities.
Security vulnerability tools scanners from Nessus, OpenVAS, Qualys, Tenable.io and Rapid7 InsightVM are among the top options to consider for identifying security weaknesses across IT environments. Selecting the right tool depends on specific organizational needs and resources.
Key Benefits of Using a Vulnerability Scanner
Security vulnerability tools provide several important benefits that make them a critical component of an effective cybersecurity strategy:
Proactively Identify Vulnerabilities
The key advantage of using a vulnerability scanner is that it allows you to proactively identify security weaknesses before hackers can exploit them. By scanning your systems and networks, you can detect misconfigurations, unpatched software, and other flaws that create risk. This gives you the opportunity to address issues before they lead to a breach.
Reduce Risk of Breaches
By finding and remediating vulnerabilities, you significantly reduce your organization’s exposure to cyber attacks. Security vulnerability tools enable you to shore up security holes and strengthen your defenses. This makes it much harder for hackers to penetrate your systems, lowering the risk of damaging data breaches.
Improve Overall Security Posture
In addition to fixing individual vulnerabilities, using a scanner improves your overall security posture. It provides visibility into where you have weaknesses and helps you benchmark security over time. You can use vulnerability trends to direct security improvements and make strategic investment decisions.
Meet Compliance Requirements
Many industry regulations and standards require vulnerability scanning as part of compliance. This includes payment card industry (PCI) standards, healthcare regulations like HIPAA, and government mandates such as FedRAMP. Using a scanner provides evidence that you are proactively auditing for risks.
Increase Efficiency vs. Manual Testing
Conducting manual vulnerability testing is extremely time-intensive and inefficient. Scanners automate the process of identifying misconfigurations and unpatched systems across the entire network. This frees up IT resources and enables continuous, scalable auditing that isn’t feasible with manual pen testing alone.
Potential Drawbacks and Challenges
While vulnerability scanners are extremely useful tools, they also come with some potential drawbacks and challenges:
- False positives – Vulnerability scanners can sometimes generate false positives by incorrectly flagging vulnerabilities that don’t actually exist. This can occur due to misconfigurations, outdated detection rules, or other errors. Dealing with excessive false positives can waste security teams’ time and resources.
- Needs frequent updating/tuning – The scanning engines and detection rules need to be frequently updated to identify the latest vulnerabilities and reduce false positives. Proper tuning is required to customize scans for an organization’s specific environment. This maintenance can be time-consuming for security teams.
- Credential management – For deeper, authenticated scanning, the scanner needs administrative credentials to access systems and scan more thoroughly. Managing and securing these credentials adds complexity.
- Can’t find all issues – While scanners are useful for identifying many vulnerabilities, they have limitations. Critical thinking and manual testing by skilled security professionals is still required to find certain issues. Scanners complement but don’t replace activities like penetration testing.
So while vulnerability scanners are very valuable for identifying security weaknesses, organizations need to weigh these potential downsides. Proper use, maintenance and integration into the broader security program is key to maximize their benefits while minimizing drawbacks.
Best Practices for Using a Vulnerability Scanner
Getting the most out of your vulnerability scanner requires following some key best practices:
- Have a scanning policy/schedule – The most effective scanning programs follow a defined policy and schedule. Determine how often to scan based on factors like your risk tolerance and asset criticality. Daily or weekly scans for critical assets may make sense.
- Authenticate scans where possible – Authenticated scans that use credentials provide more accurate results than unauthenticated scans. They can access more of your environment. Enable authenticated scans selectively based on risk.
- Customize scans based on assets – Tailor your scans to focus on specific assets or asset groups. Scanning everything can generate excessive noise. Target areas that need priority scanning.
- Integrate with ticketing systems – Integrate your scanner with your existing IT ticketing system. This allows you to automatically generate tickets for findings and track remediation.
- Review and prioritize findings – Don’t just run scans and ignore the output. Have processes to review findings, eliminate false positives, and prioritize the results based on severity and exploitability.
Following security best practices will help you get maximum effectiveness from your vulnerability scanning program. It takes more than just installing a tool. You need policies, processes, and expertise to leverage your scanner strategically.
The Future of Vulnerability Scanning
Vulnerability scanning tools are rapidly evolving to meet the growing security challenges faced by organizations. Here are some of the key trends shaping the future of vulnerability scanning:
Increasing Automation and Machine Learning
Many vulnerability scanners are incorporating advanced automation and machine learning capabilities to speed up scanning and reduce false positives. By using algorithms and statistical models, scanners can automatically identify vulnerabilities with greater accuracy. This reduces the need for manual validation and follow-up.
Integrations with Other Security Tools
Vulnerability scanners are being integrated into broader security platforms and tools like SIEMs, firewalls, and endpoint detection and response solutions. This allows vulnerability data to be correlated with other threat intelligence for faster incident response. Integrations also ensure vulnerabilities identified by scanners are remediated across an organization’s entire security infrastructure.
Cloud-based and SaaS Delivery Models
There is a shift towards cloud-based delivery models for vulnerability scanners, often via SaaS. This makes it easier to deploy scanners across an entire enterprise. Cloud-based models also enable easier and more frequent updating of vulnerability signatures. Containerization of scanners is another trend, allowing scanners to seamlessly integrate in cloud and on-prem environments.
Focus on IoT and Embedded Devices
With the growth of IoT and smart devices, vulnerability scanners are adapting to securing this emerging threat landscape. Scanners are being tuned to detect vulnerabilities in embedded devices like IP cameras, smart TVs, and connected medical devices. IoT-focused scanners will be critical for organizations to identify and patch vulnerabilities in business-critical connected devices.